Anti-Phishing Awareness

Anti-Phishing
92% of all viruses and malware are now delivered through email, due to it’s high rate of success.
By targeting email, hackers can bypass most firewalls and intrusion detection systems to gain the
information needed to access accounts. Below are some statistics that will help you remain vigilant,
as well as some resources to help raise awareness in regards to potential threats.
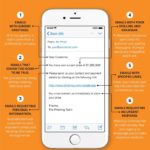
The most common disguises for malware are:
- Bill / invoice (15.9%)
- Email delivery failure (15.3%)
- Legal / law enforcement (13.2%)
- Scanned document (11.5%)
- Package delivery (3.9%)
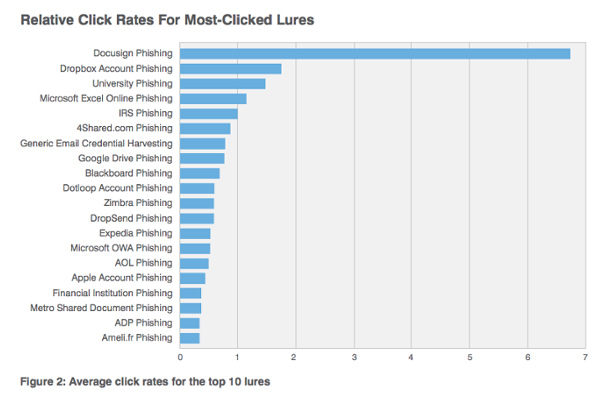
The most successful phishing campaigns are from document sharing services such as Dropbox, Docusign etc. which is illustrated in the graph below.
Downloadable/Printable Posters
Use these campaign posters to arm yourself with the knowledge you need to thwart potential attacks.
Security Awareness Videos
Here’s some short videos that will teach you the fundamentals of identifying a phishing attempt or scam. Empower yourself with the knowledge to stay safe online.
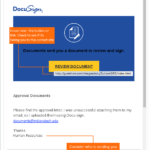
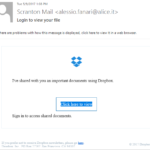
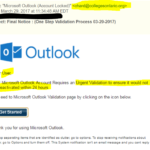
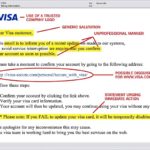
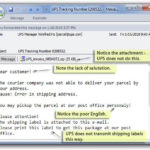
Sample Phishing Emails
Here’s some examples of the most common phishing attempts. These are designed to get the user to enter sensitive information such as usernames/passwords, credit card information, bank account numbers etc.
REMEMBER: IF YOU DON’T EXPECT IT, REJECT IT!